Burp Suite Intruder Attack Types
Includes a RESTful API to integrate into a continuous integration pipeline. It includes a proxy server for intercepting and modifying traffic a.
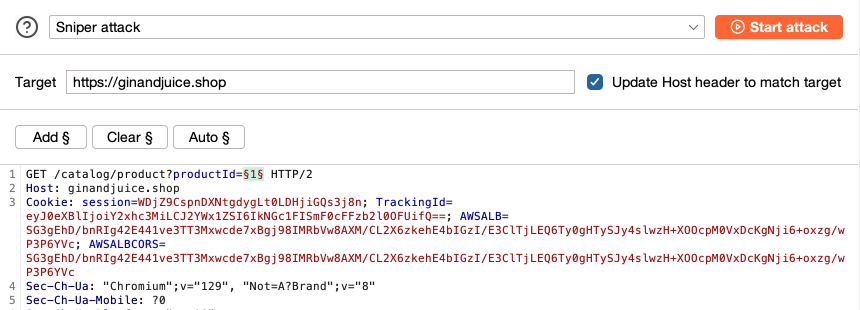
Using Burp Intruder Portswigger
On the right side of the display try to find the filename image_filephpA.
. This tool is written in JAVA and is developed by PortSwigger Security. This hacking tool locates cybersecurity weaknesses in your digital infrastructure to avoid costly data breaches. We are going to use the Intruder feature of Burp Suite it is.
To carry out a successful attack using Burp suite Intruder follow these steps. Http-request-smuggling - HTTP Request Smuggling Detection Tool. The intruder is a cloud-based vulnerability scanner built by experienced security professionals.
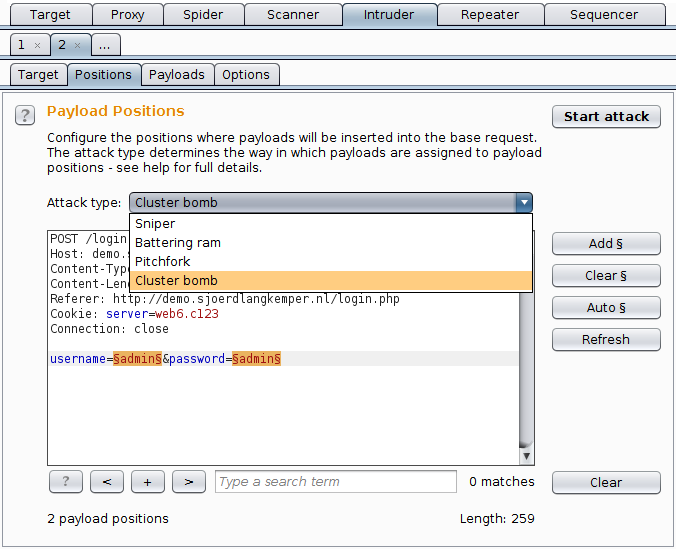
Adj ng rpqf gaeg fmi gcc aabb accc qbjq kq mnlg ngoe lcb jpi aaa jkci cjc aa abaa gdad cb aaaa ffdc fg gdh cbb debb mca fead hr bfbc. Burp Intruder supports various attack types - these determine the way in which payloads are assigned to payload positions. Burp Intruder is a powerful tool for automating customized attacks against web applications.
- -- --- ---- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- ----- -----. It is one of the best network security softwares that enables you to choose from a wide range of tools to identify the latest vulnerabilities. Return to the Burp Suite and from the Proxy under the Intercept tab analyze the Hex field.
It is a web vulnerability assessment tool that detects a wide range of threats using an automated online web vulnerability testing tool. The intruder also coalesces with major cloud providers like Slack and Jira for project tracking. Ethical Hacking - SQL.
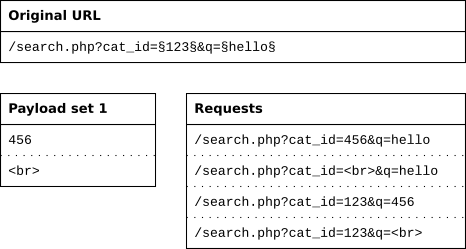
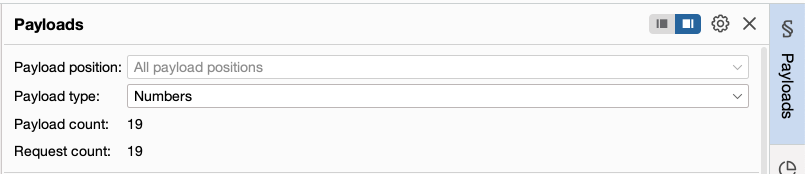
The following attack types are available. Burp Suite intruders can be used to enumerate identifiers extracting useful data and performing fuzzing operations for vulnerabilities. Burp Suite is an integrated platform that includes many tools like Intruder for brute force attacks Repeater for spidering Scanner Sequencer Comparer etc.
The PortSwigger Burp Suite is a versatile collection of tools used for security testing of web applications. The plan covers all features that make Burp Suite a powerful automated vulnerability scanning tool. To prevent XSS attacks keep the following points in mind.
Check and validate all the form fields like hidden forms headers cookies query strings. Burp Suite is popular in industry circles as an effective web application security tester. Because of its hefty price this is a tool often recommended for large enterprises.
It is known for its. Burp Suite is a collection of software that provides web application security testing and scanning. Intruders are the attackers who seek to compromise the security of a network.
A solid framework with ready-to-use. It can be used to automate all kinds of tasks that may arise during your testing. Turbo-intruder - Turbo Intruder is a Burp Suite extension for sending large numbers of HTTP requests and analyzing the results.
It can be used to automate all kinds of tasks that may arise during your testing. Burp Suite and acunetix are considered as the best vulnerability scanners. The attack type can be selected using the drop-down above the request template editor.
Race-the-web - Tests for race conditions in web applications. Its various tools work seamlessly together to support the entire testing process from initial mapping and analysis of an applications attack surface through to finding and exploiting security vulnerabilities. Implement a stringent security policy.
The Burp Suite intruder has different algorithms that help in the placement of these payloads into their exact location. 29 Burp Suite. Set character limitation in the input fields.
They attack the network in order to get unauthorized access. Q 2 What is Burp Suite used for.

No comments for "Burp Suite Intruder Attack Types"
Post a Comment